Shield Your Containers: Trivy Installation and Vulnerability Scanning
In the current DevOps and cloud-native ecosystem, containerized applications are widely used to ensure scalability, efficiency, and reliability.
1. Why We Need This Use Case
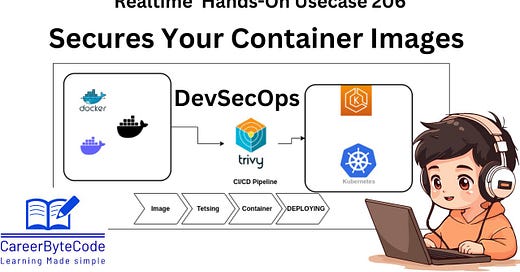
In the current DevOps and cloud-native ecosystem, containerized applications are widely used to ensure scalability, efficiency, and reliability. However, containers can introduce security vulnerabilities, including outdated libraries, exposed credentials, or unpatched software. Security scanning tools like Trivy are essential to maintain a secure environment by detecting vulnerabilities before applications are deployed into production. This ensures compliance with security standards, prevents exploitation, and promotes a secure software development lifecycle (SDLC).
Trivy is a versatile and comprehensive open-source security scanner that helps to identify vulnerabilities in container images, filesystems, and more, offering an efficient way to keep your environment safe.
2. When We Need This Use Case
When you need to scan container images before deploying them to production to ensure they are free of vulnerabilities.
During the development cycle, as part of your CI/CD pipeline to identify security issues early in the process.
When working with open-source base images from Docker Hub or other registries that could have unknown vulnerabilities.
To maintain continuous security monitoring on images used in Kubernetes or Docker environments.
When deploying an image to environments like AWS, Kubernetes, or container orchestration tools.
3. Challenge Scenarios
Keep reading with a 7-day free trial
Subscribe to CareerByteCode’s Substack to keep reading this post and get 7 days of free access to the full post archives.