Compliance-First Architecture: Implementing Azure Private Endpoints for Storage
Locking Down Storage Access: Enforcing Private-Only Data Flows in Azure
1. Problem Statement :
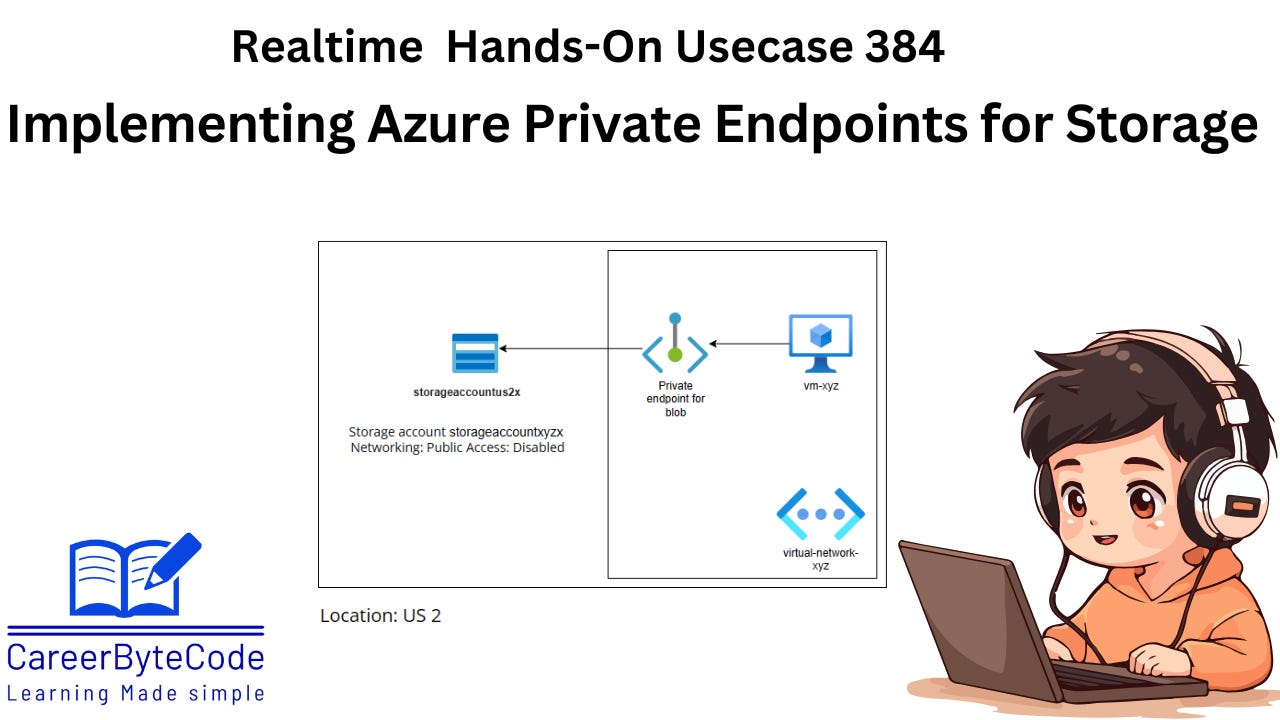
A fintech app runs on Azure VMs inside a VNet. It processes sensitive customer documents and stores them in Azure Blob Storage. Due to new compliance mandates, any data transfer over the public internet is forbidden. All traffic, including access to the storage account, must stay inside the Microsoft network no exceptions. Right now, the storage account is reachable publicly, which is a compliance risk and a potential attack vector.
Right now, the application’s virtual machines are accessing the Azure Storage Account using its public endpoint. This means traffic between the VM and Storage could traverse the public internet even if only for a moment making your data potentially visible, interceptable, or vulnerable to man-in-the-middle attacks. On top of that, organizations in finance, healthcare, or other regulated industries are often legally required to prove that sensitive data never leaves private, controlled networks.
This use case solves all of that.
It blocks all public internet access to the Storage Account.
It enforces that all storage access happens only through Azure’s private backbone using a Private Endpoint, mapped to a private IP in your VNet.
It removes the risk of accidental data exposure, helps pass strict compliance audits, and dramatically reduces attack surface by keeping storage access off the public internet.
What this really means:
You’re addressing both a security vulnerability (public exposure of storage) and a compliance gap (lack of enforced private-only data paths). This pattern guarantees that only your VMs or whatever resources are inside your VNet and allowed by NSG rules can reach the Storage Account, and no one else can, not even accidentally.
2. Why We Need This Use Case
Standard Azure Storage endpoints are public by default, which is a problem if you need airtight security or must answer to auditors. If traffic from your app to your storage account ever leaves the Azure backbone, you risk data leakage, non-compliance, and exposure to internet-based attacks. Private Endpoints guarantee storage traffic is locked to private IPs inside your own VNet, with nothing exposed to the outside world. It also means you can actually prove to auditors and your security team that data never leaves Microsoft’s backbone.
This use case demonstrates how to enforce true network isolation for cloud storage in Azure. It’s not just about locking down a storage account—it’s about showing, step by step, how to:
Cut off all public endpoints for storage access so data isn’t exposed, even by mistake.
Build an end-to-end private connectivity path from your application’s VMs to your storage account, using Azure Private Endpoint.
Prove that name resolution and traffic routing stay private with Private DNS Zones and NSG rules.
Test and validate that the only way to reach storage is through private IPs no shortcuts, no back doors.
In short, it’s a practical demo of how to design for least privilege network access in Azure, enforce compliance policies, and actually verify (not just assume) that your storage access is fully private. This pattern is reusable anywhere you need airtight control over who and what can touch your data at the network level.
3. When We Need This Use Case
When you’re handling regulated or highly confidential data (think finance, healthcare, or government workloads)
When your security policy or auditor mandates “no public exposure” for storage accounts
If you want to tightly restrict access at the network layer, not just by SAS or RBAC
If your VMs or services need to access storage accounts securely without punching holes in NSGs or using service endpoints, which still allow some public access